When people think about their strategic IT security projects, they often think of the last incident they were affected of and try to mitigate that, often by using technology only.
This is a valid approach and probably is not so wrong, because we often see waves of incidents rolling in, the wannacry wave, other ransomware waves, certain exploit kits or malware waves. So it makes some sense to concentrate on those threats when they happen. Of course you should have done something long before it hit you or other people, but the nature of IT security is that this hardly ever happens.
I closely follow the use of Mitre ATT&CK and find it very useful in approaching the threats you are facing and looking for mitigations.
What is MITRE ATT&CK?
You can read all about Mitre ATT&CK, but here is the short version. ATT&CK is a open, comprehensible knowledge base about threat actor tactics and techniques. It is a great tool for modeling your threats and looking at what mitigations really make sense and finding the right mitigations.
Here is a great example of the matrix and how it looks.
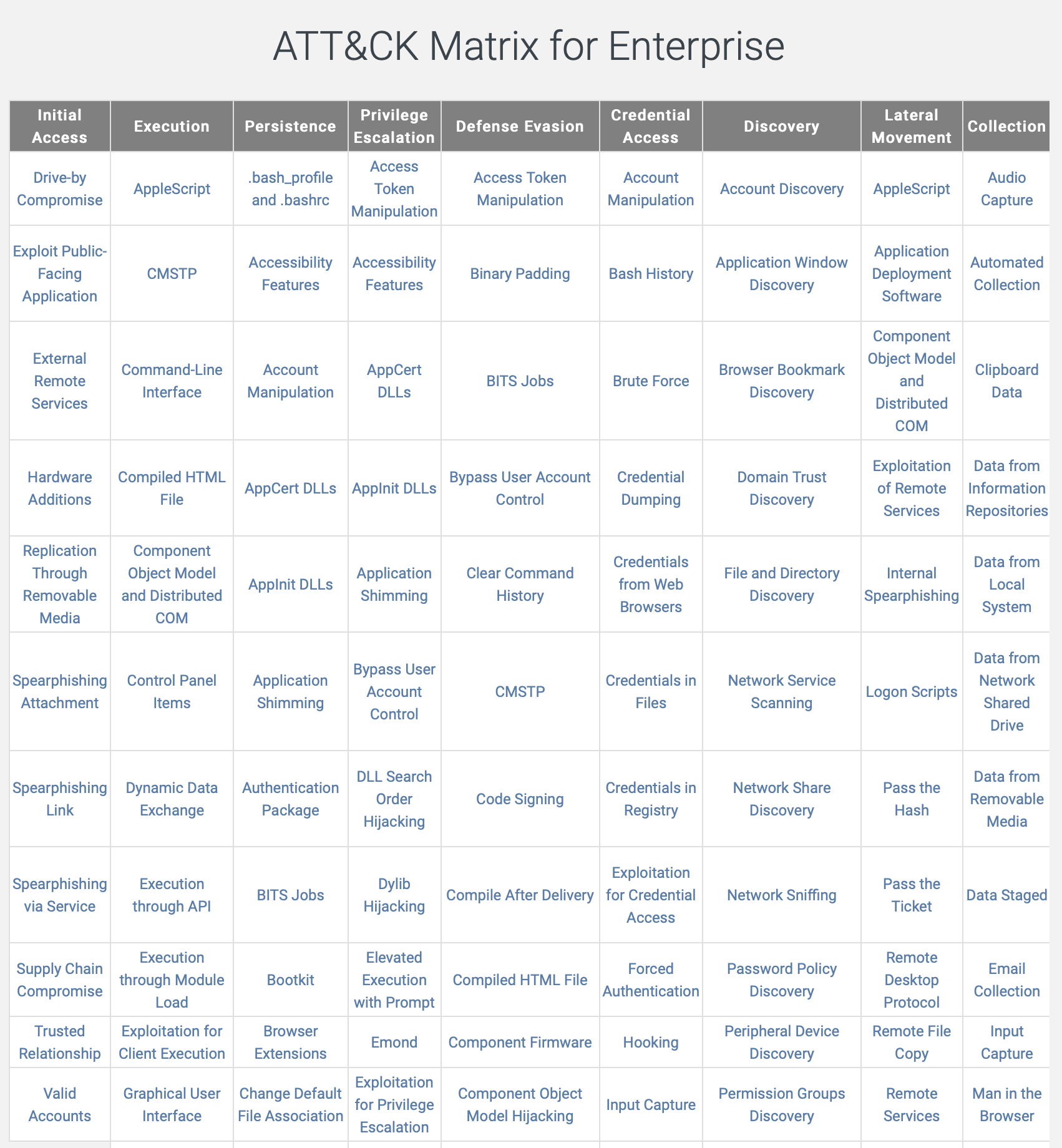
Mitre ATT&CK is made up of 3 main categories
- Tactics
- Techniques
- Mitigations
Let’s look at what they are about first.
Tactics
Tactics are made up of 9 subcategories and are closely related to the threat life cycle.
Techniques
Techniques is the most complex taxonomy and describes the technical processes attackers use in a specific tactic, it’s things like specifics on how to get to credentials (e.g. Credentials from web browsers) or how to gain persistence in a network or on a workload (e.g. become a login item automatically executed at login).
Mitigations
Mitigations are the most interesting part after you found out what your threats are and what techniques may be used. For each of the above techniques ATT&CK suggests mitigations.
Below is a typical example on how to mitigate a technique called Service Stop.
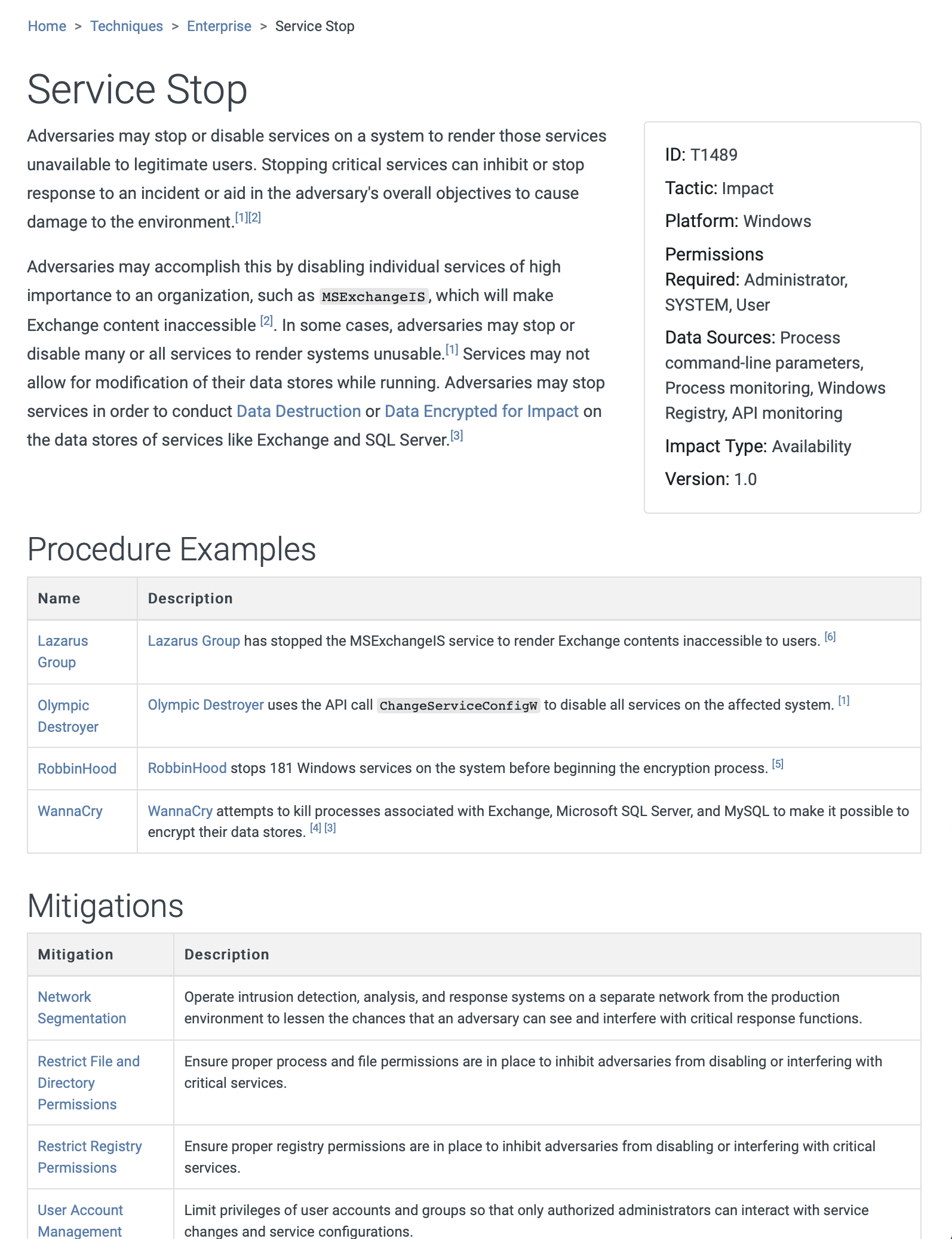
How can it help me?
When you think of any of the threats that you are facing, you will probably struggle to think of all the techniques people are using to get to their objectives. ATT&CK helps you in identifying all of those and will also suggest mitigations for them. It is a great tool to become more data driven and to find a structured approach in extending your security posture.
I would suggest a strategic approach in implementing mitigations and use available tools like the Mitre ATT&CK Navigator to navigate around. The navigator also implements scoring techniques and is very powerful in creating layers of techniques that you can combine later on with scores.
The power of network segmentation (and security segmentation)
I used the above mentioned navigator to mark all the techniques that can be mitigated by using network segmentation as suggested by Mitre ATT&CK and the power of segmentation becomes visible in the attack lifecycle.
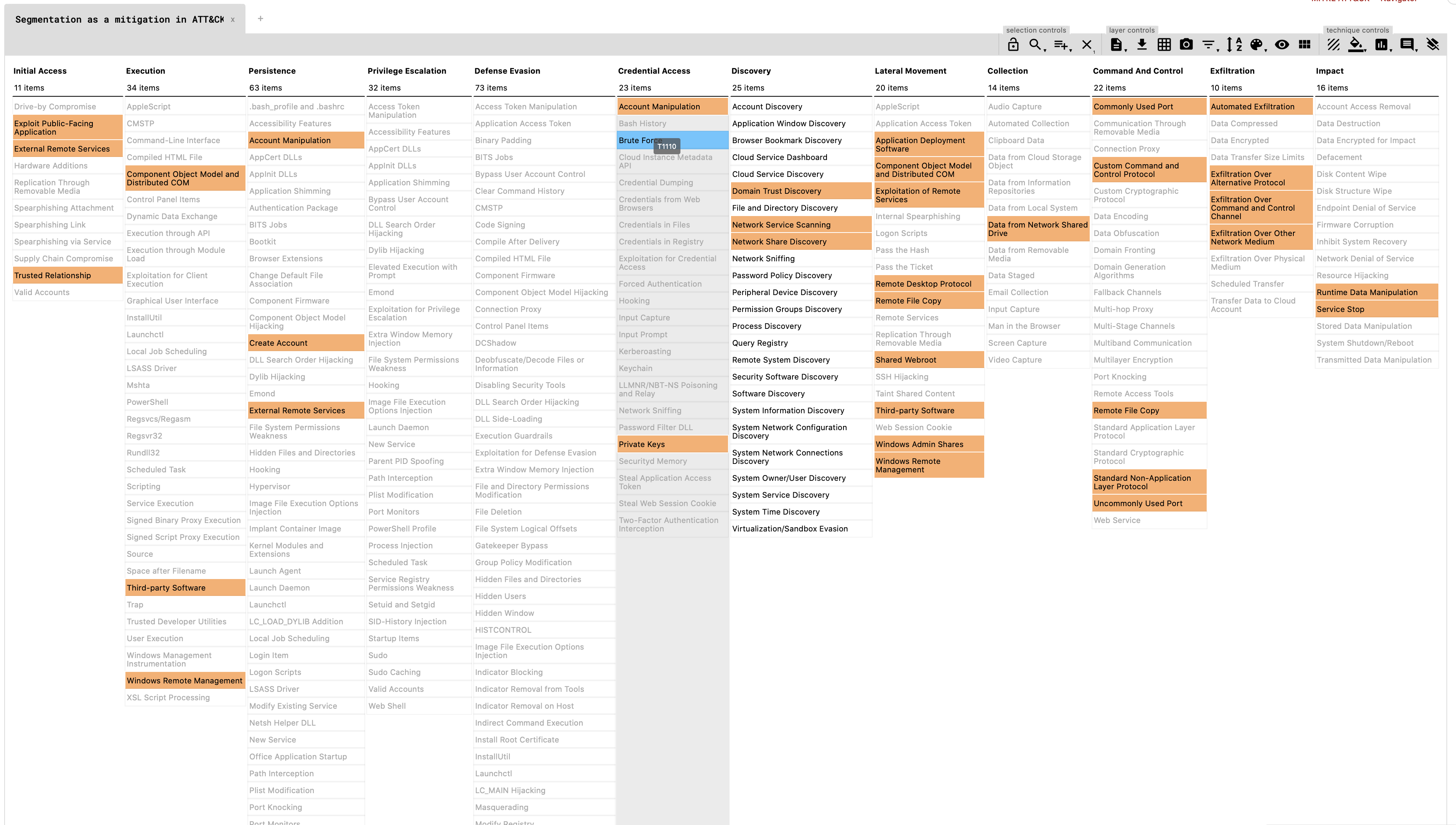
You can also use this MITRE ATT&CK navigator link to access my custom MITRE ATT&CK navigator from the above image. Have fun playing with it.
